The Spanish developer j0lama, who for recall holds a PlayStation 4 under firmware 1.76, offers for a few hours http://jolama.es/temas/ps4me/index.php Who explains the basics of a tool called PS4ME.
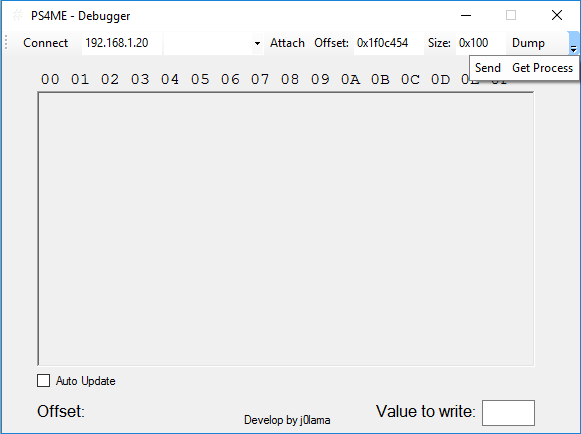
Under this name hides a payload that takes the form of a PS4ME.dll, and that it should be launched with the exploit webkit developed by cTurt known as dlclose.
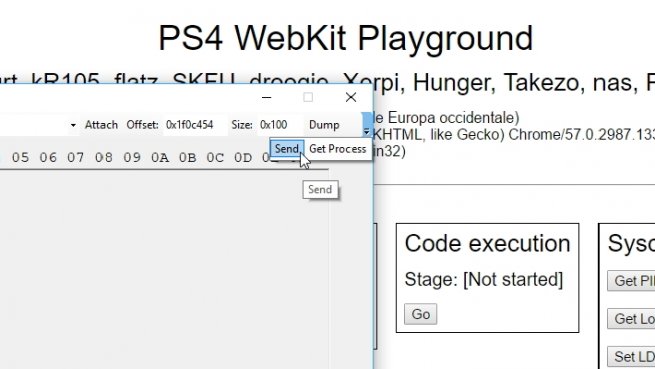
The library is similar in some respects to the PS3Lib.dll libraries for CCAPI and TMAPI, it works as a program that allows to read and write processes in memory.
To execute it is very simple, just run the code execution operation via PS4Playground, then click send to send the PS4ME-Playload.bin file inside the console, then Update process say "Get Process" which will show the process corresponding to your game (Eboot.bin and default_mp.elf).
Description
-----------
As I said in my previous post on RTM on PS4, my main goal is to develop a system similar to PS3TMAPI / PS3CCAPI but for PS4 that is simple to use and so developers can create their own tools.
This project I want it to be a community project and that all people who want to collaborate to improve the system contact me and so I can create a team.
PS4ME.dll is a Windows library with all the necessary functions to be able to link to a PS4 (Version 1.76 for now) and to be able to read / write process memory.
For now it only has the following functions:
- SendPayload (string IP, string payloadPath): Allows to send a payload to a certain IP through port 9023 so that it can be executed by the PS4 Playground of cTurt.
- Connect (string ip): Connects to the PS4 with the specified IP.
- Disconnect (): Disconnects from the PS4.
- string [] getProcesses (): Gets an array of processes that are currently running on the PS4.
- string AttachProcess (string ProcessName): Link to a given process returning an error message in case of failure.
- byte [] dumpMemory (string Offset, string size): Performs a memory dump of the specified size and starts in the memory address specified by the offset returning the byte array.
- writeMemory (string Offset, string value): Write in the memory address specified by Offset a byte specified by value.
- string readMemory (String Offset): Returns the read byte of the memory location specified by Offset.
As soon as I have time I will be adding more functions to get more data about the processes (size, addresses, permissions, etc).
I also include a Payload add-on to PS4ME.dll which is what will run on the PS4 allowing all PS4ME functions to be successful. It is recommended that a payload be executed before starting any game since it deactivates the ASLR and spoofs the console to avoid that updates are made when starting the games.
PS4METool
---------
I have created this simple application for Windows that works with PS4ME.dll as a demonstration.
Once the application has started, we have to activate the code execution on PS4 from PS4 Playground and in the options bar open the right drop-down and give to Send. This will send the payload to the PS4 that will start running.
Once this is done we can give you to connect and update the process list with the Get Process button when we are inside the game so we can see the process corresponding to our game (eboot.bin / default_mp.elf).
Once we have selected the process we give Attach to link and we can select a memory address and a size and give Dump to see the memory. We can check the Auto Update check box so that the memory is updated every 0.4 seconds. If we want to write in a memory address write the value of the byte down to the left and double click on the value that we want to overwrite.
Download
https://www.virustotal.com/en/file/...704344283e7e2d1404cb17e0/analysis/1492101177/

Under this name hides a payload that takes the form of a PS4ME.dll, and that it should be launched with the exploit webkit developed by cTurt known as dlclose.

The library is similar in some respects to the PS3Lib.dll libraries for CCAPI and TMAPI, it works as a program that allows to read and write processes in memory.
To execute it is very simple, just run the code execution operation via PS4Playground, then click send to send the PS4ME-Playload.bin file inside the console, then Update process say "Get Process" which will show the process corresponding to your game (Eboot.bin and default_mp.elf).
Description
-----------
As I said in my previous post on RTM on PS4, my main goal is to develop a system similar to PS3TMAPI / PS3CCAPI but for PS4 that is simple to use and so developers can create their own tools.
This project I want it to be a community project and that all people who want to collaborate to improve the system contact me and so I can create a team.
PS4ME.dll is a Windows library with all the necessary functions to be able to link to a PS4 (Version 1.76 for now) and to be able to read / write process memory.
For now it only has the following functions:
- SendPayload (string IP, string payloadPath): Allows to send a payload to a certain IP through port 9023 so that it can be executed by the PS4 Playground of cTurt.
- Connect (string ip): Connects to the PS4 with the specified IP.
- Disconnect (): Disconnects from the PS4.
- string [] getProcesses (): Gets an array of processes that are currently running on the PS4.
- string AttachProcess (string ProcessName): Link to a given process returning an error message in case of failure.
- byte [] dumpMemory (string Offset, string size): Performs a memory dump of the specified size and starts in the memory address specified by the offset returning the byte array.
- writeMemory (string Offset, string value): Write in the memory address specified by Offset a byte specified by value.
- string readMemory (String Offset): Returns the read byte of the memory location specified by Offset.
As soon as I have time I will be adding more functions to get more data about the processes (size, addresses, permissions, etc).
I also include a Payload add-on to PS4ME.dll which is what will run on the PS4 allowing all PS4ME functions to be successful. It is recommended that a payload be executed before starting any game since it deactivates the ASLR and spoofs the console to avoid that updates are made when starting the games.
PS4METool
---------
I have created this simple application for Windows that works with PS4ME.dll as a demonstration.
Once the application has started, we have to activate the code execution on PS4 from PS4 Playground and in the options bar open the right drop-down and give to Send. This will send the payload to the PS4 that will start running.
Once this is done we can give you to connect and update the process list with the Get Process button when we are inside the game so we can see the process corresponding to our game (eboot.bin / default_mp.elf).
Once we have selected the process we give Attach to link and we can select a memory address and a size and give Dump to see the memory. We can check the Auto Update check box so that the memory is updated every 0.4 seconds. If we want to write in a memory address write the value of the byte down to the left and double click on the value that we want to overwrite.
Download
https://www.virustotal.com/en/file/...704344283e7e2d1404cb17e0/analysis/1492101177/