These are still important advances on the long road which will lead us one day to the doors of happiness. The developer Specter as promised informs us via his Twitter profile that he finally managed to carry the feat of qwertyoruiopz on most of the latest firmwares offered by Sony.
He says he has ported the firmware code 3.50, 3.55, 3.70, 4.00, 4.06 and 4.07, yes you read correctly, so there is the 3.50 and 4.07.
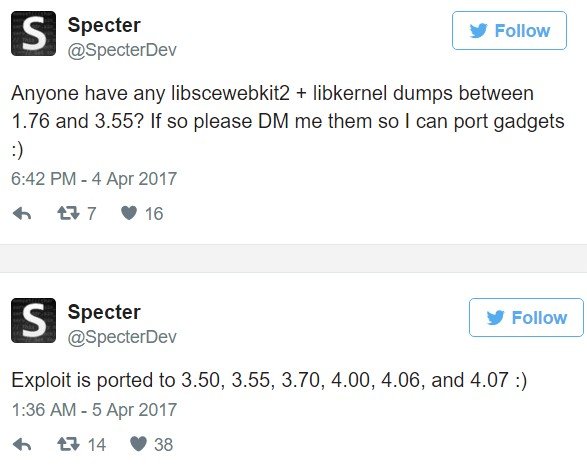
It is surprising to see the 4.07, but it is now confirmed the fault walks on the 4.07, and of course as we showed our friend Markus the feat is compatible with the PS4 Pro under firmware 3.70.
Markus offers us the video of the exploit under firmware 4.07:
Organization
Files in order by name alphabetically;
expl.js - Contains the heart of the exploit and establishes a read/write primitive.
gadgets.js - Contains gadget maps and function stub maps for a variety of firmwares. Which map is used is determined in the post-exploitation phase.
index.html - The main page for the exploit. Launches the exploit and contains post-exploitation stuff, as well as output and code execution.
rop.js - Contains the ROP framework modified from Qwerty's original exploit as well as the array in which module base addresses are held and gadget addresses are calculated.
syscalls.js - Contains a system call map for a variety of firmwares as well as a 'name -> number' map for syscall ID's.
Usage
Simply setup a web-server on localhost using xampp or any other program and setup these files in a directory. You can then go to your computer's local IPv4 address (found by running ipconfig in cmd.exe) and access the exploit.
Notes
The exploit is pretty stable but will still sometimes crash. If the browser freezes simply back out and retry, if a segmentation fault (identified by prompt "You do not have enough free system memory") occurs, refresh the page before trying again as it seems to lead to better results.
This only allows code execution in ring3, to get ring0 execution a kernel exploit and KROP chain is needed.
If I've made an error (particularly having to do with firmware compatibility and gadgets) feel free to open an issue on the repo.
The exploit has been tested on 3.55 and 4.00, it is assumed to work on other firmwares listed but not guaranteed, again if you encounter a problem - open an issue on the repo.
It is necessary to keep in mind that qwertyoruiopz is forced to work on a firmware so as not to scatter and especially since it also does not have 10 different consoles ... its firmware is 4.06, so All the tests and the Poc are made from this firmware, leaving the charge to the other developers to adapt it to other firmwares if they wish, besides some like Cryptogenic works on the 3.15.
Source link: PS4-4.0x-Code-Execution-PoC https://github.com/Cryptogenic/PS4-4.0x-Code-Execution-PoC
He says he has ported the firmware code 3.50, 3.55, 3.70, 4.00, 4.06 and 4.07, yes you read correctly, so there is the 3.50 and 4.07.

It is surprising to see the 4.07, but it is now confirmed the fault walks on the 4.07, and of course as we showed our friend Markus the feat is compatible with the PS4 Pro under firmware 3.70.
Markus offers us the video of the exploit under firmware 4.07:
Organization
Files in order by name alphabetically;
expl.js - Contains the heart of the exploit and establishes a read/write primitive.
gadgets.js - Contains gadget maps and function stub maps for a variety of firmwares. Which map is used is determined in the post-exploitation phase.
index.html - The main page for the exploit. Launches the exploit and contains post-exploitation stuff, as well as output and code execution.
rop.js - Contains the ROP framework modified from Qwerty's original exploit as well as the array in which module base addresses are held and gadget addresses are calculated.
syscalls.js - Contains a system call map for a variety of firmwares as well as a 'name -> number' map for syscall ID's.
Usage
Simply setup a web-server on localhost using xampp or any other program and setup these files in a directory. You can then go to your computer's local IPv4 address (found by running ipconfig in cmd.exe) and access the exploit.
Notes
The exploit is pretty stable but will still sometimes crash. If the browser freezes simply back out and retry, if a segmentation fault (identified by prompt "You do not have enough free system memory") occurs, refresh the page before trying again as it seems to lead to better results.
This only allows code execution in ring3, to get ring0 execution a kernel exploit and KROP chain is needed.
If I've made an error (particularly having to do with firmware compatibility and gadgets) feel free to open an issue on the repo.
The exploit has been tested on 3.55 and 4.00, it is assumed to work on other firmwares listed but not guaranteed, again if you encounter a problem - open an issue on the repo.
It is necessary to keep in mind that qwertyoruiopz is forced to work on a firmware so as not to scatter and especially since it also does not have 10 different consoles ... its firmware is 4.06, so All the tests and the Poc are made from this firmware, leaving the charge to the other developers to adapt it to other firmwares if they wish, besides some like Cryptogenic works on the 3.15.
Source link: PS4-4.0x-Code-Execution-PoC https://github.com/Cryptogenic/PS4-4.0x-Code-Execution-PoC