The encryption "root keys" for the PlayStation 5 were acquired, according to an announcement made by the hacking group Fail0verflow on Sunday night. This is a crucial first step in any attempt to unlock the console and enable users to run homebrew software.
An snapshot of what seems to be the PS5's decrypted firmware files, highlighted in code that refers to the system's "secure loader," is included in the tweeted announcement. By dissecting that encrypted firmware, Fail0verflow (or other hackers) might be able to produce custom firmware that can load homebrew PS5 programmes that have been signed with those same symmetric keys so that the PS5 will accept them as genuine.
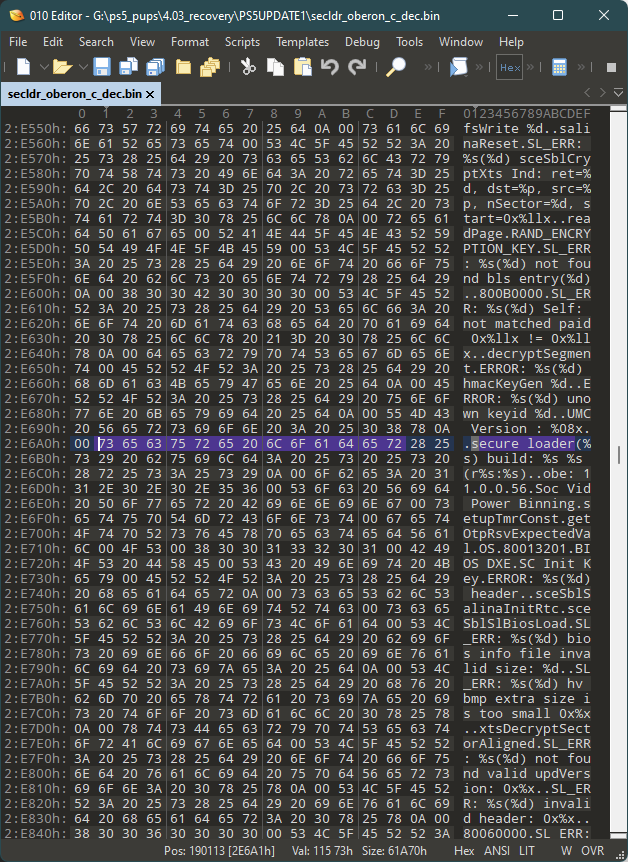
Separate asymmetric keys are required to verify any homebrew software for it to be recognised as genuine by the system, in addition to the symmetric encryption/decryption keys that have reportedly been revealed. It doesn't appear that the private section of those authentication keys has been discovered yet, and it most likely won't be discovered on the system itself either. Nevertheless, the in question symmetric keys should be helpful for enabling further study of the PS5 system software and identifying more flaws that would permit the execution of unsigned code. Ars is sorry for the error.
Both removing the system software from the PS5 and installing a replacement call for some kind of vulnerability that grants read and/or write access to the typically secure kernel of the PS5. The exploit the group utilised is not described in Fail0verflow's report, however, the tweet claims that the keys were "obtained from software," indicating that the organisation didn't need to alter the hardware itself.
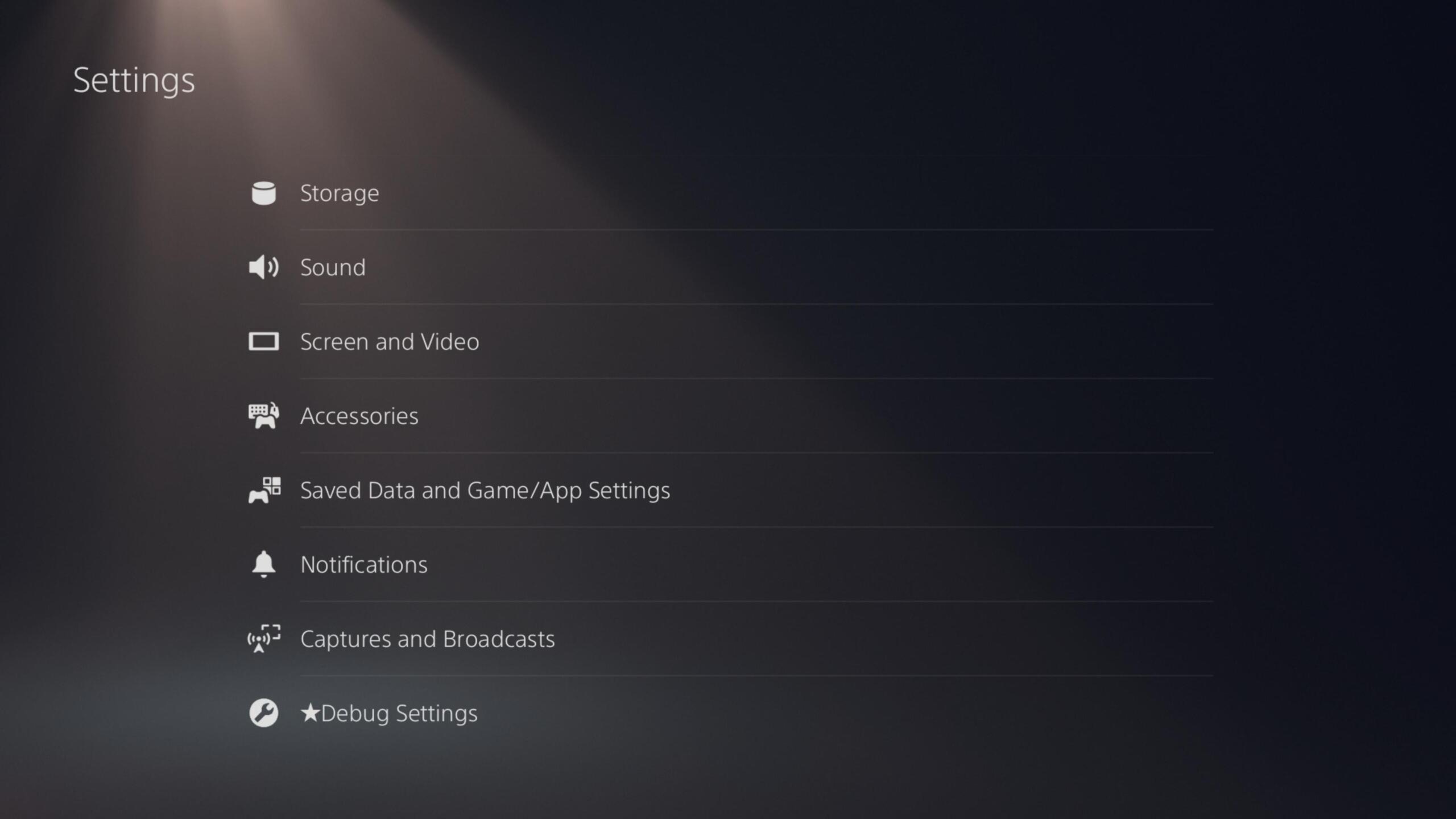
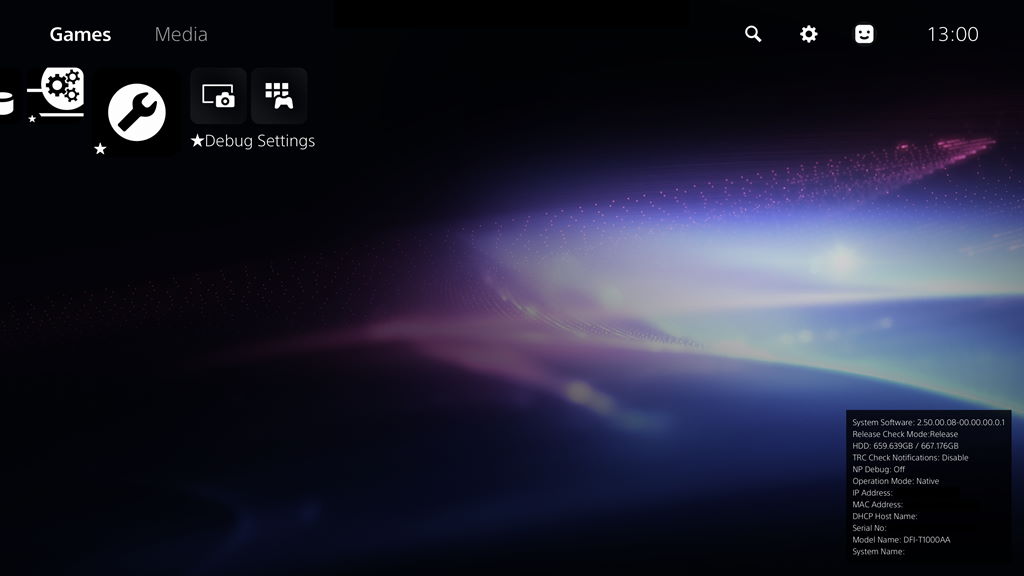
This past weekend, well-known PlayStation hacker theFlow0 shared a screenshot on Twitter that revealed a "Debug Settings" option among the standard list of PS5 settings. This debug setting was previously only accessible on development hardware, where the GUI has a very different appearance, according to the console-hacking news website Wololo. However, TheFlow0's tweet appears to have originated from a retail PS5's built-in sharing feature, indicating that he also utilised an attack to activate the internal flags that unlock the mode on common consumer hardware
As you all know this kind of exploit mid 2011 for the ps3 was massive it allowed us to run unassigned code it allowed us to run home brew etc this kind of exploit can not be patched.
An snapshot of what seems to be the PS5's decrypted firmware files, highlighted in code that refers to the system's "secure loader," is included in the tweeted announcement. By dissecting that encrypted firmware, Fail0verflow (or other hackers) might be able to produce custom firmware that can load homebrew PS5 programmes that have been signed with those same symmetric keys so that the PS5 will accept them as genuine.

Separate asymmetric keys are required to verify any homebrew software for it to be recognised as genuine by the system, in addition to the symmetric encryption/decryption keys that have reportedly been revealed. It doesn't appear that the private section of those authentication keys has been discovered yet, and it most likely won't be discovered on the system itself either. Nevertheless, the in question symmetric keys should be helpful for enabling further study of the PS5 system software and identifying more flaws that would permit the execution of unsigned code. Ars is sorry for the error.
Both removing the system software from the PS5 and installing a replacement call for some kind of vulnerability that grants read and/or write access to the typically secure kernel of the PS5. The exploit the group utilised is not described in Fail0verflow's report, however, the tweet claims that the keys were "obtained from software," indicating that the organisation didn't need to alter the hardware itself.
This past weekend, well-known PlayStation hacker theFlow0 shared a screenshot on Twitter that revealed a "Debug Settings" option among the standard list of PS5 settings. This debug setting was previously only accessible on development hardware, where the GUI has a very different appearance, according to the console-hacking news website Wololo. However, TheFlow0's tweet appears to have originated from a retail PS5's built-in sharing feature, indicating that he also utilised an attack to activate the internal flags that unlock the mode on common consumer hardware


As you all know this kind of exploit mid 2011 for the ps3 was massive it allowed us to run unassigned code it allowed us to run home brew etc this kind of exploit can not be patched.